Rapid7 researchers have discovered two critical vulnerabilities in JetBrains TeamCity – a popular build management and continuous integration/delivery (CI/CD) server. Given the server’s large user base and the low attack complexity of the vulnerabilities, mitigation should become a high priority for all users.
Overview
With a Common Vulnerability Scoring System (CVSS) score of 9.8, rated as critical, the first security flaw (CVE-2024-27198) is classified as an authentication bypass vulnerability. This means that, if exploited, it could allow an unauthenticated attacker to bypass authentication checks and gain admin control of the TeamCity server.
The second (CVE-2024-27199) could enable limited authenticated endpoint access to malicious actors, without the need to gain proper authentication. They could then be free to modify system settings and access sensitive server information.
The first vulnerability (CVE-2024-27198) has been actively exploited. It’s now been added to the CISA Known Exploited Vulnerabilities catalog, a compilation of security flaws that have been successfully exploited that works to help the cybersecurity community better manage threats. Both vulnerabilities affect all TeamCity On-Premises versions up to and including 2023.11.3.
Mitigation options
Option 1: Update your JetBrains version
JetBrains has fixed these vulnerabilities for version 2023.11.4. You can download this latest version to update your server or simply select ‘automatic update’ within TeamCity.
Option 2: Download a security patch plugin
If you’re unable to update your version of JetBrains, a security patch plugin is available. The plugin can be installed on all TeamCity versions through 2023.11.3. This temporary measure ensures that vulnerabilities are addressed until the server can be updated.
You can download the security patch plugin for:
We always recommend upgrading your server to the latest version if possible. That way, you can benefit from all the up-to-date security measures.
Technical description of vulnerabilities
Vulnerability 1: CVE-2024-27198
The security flaw resides in the functionality of the jetbrains.buildServer.controllers.BaseController class of the web-openapi.jar library.
This vulnerability enables bad actors to bypass the authentication checks by crafting specific URL requests to the web server, enabling them to access endpoints that are supposed to be secure and authenticated.
Cataloged as an alternate path weakness (CWE-288), this issue can be exploited by crafting a URL against an unauthenticated non-existing page which causes the controller to route a 404 response. Then, by supplying an HTTP query parameter named “jsp” containing the value of an authenticated URI path ending with “;.jsp”, it is possible to access the restricted endpoint.
Vulnerability 2: CVE-2024-27199
A path traversal flaw in some endpoints could enable malicious actors to gain unauthenticated access. These endpoints include /res/, /update/, and /.well-known/acme-challenge/.
Attackers could use these paths in conjunction with path traversal vectors to bypass authentication checks, leading to a limited amount of information disclosure and system modification.
Proof of Concept (PoC)
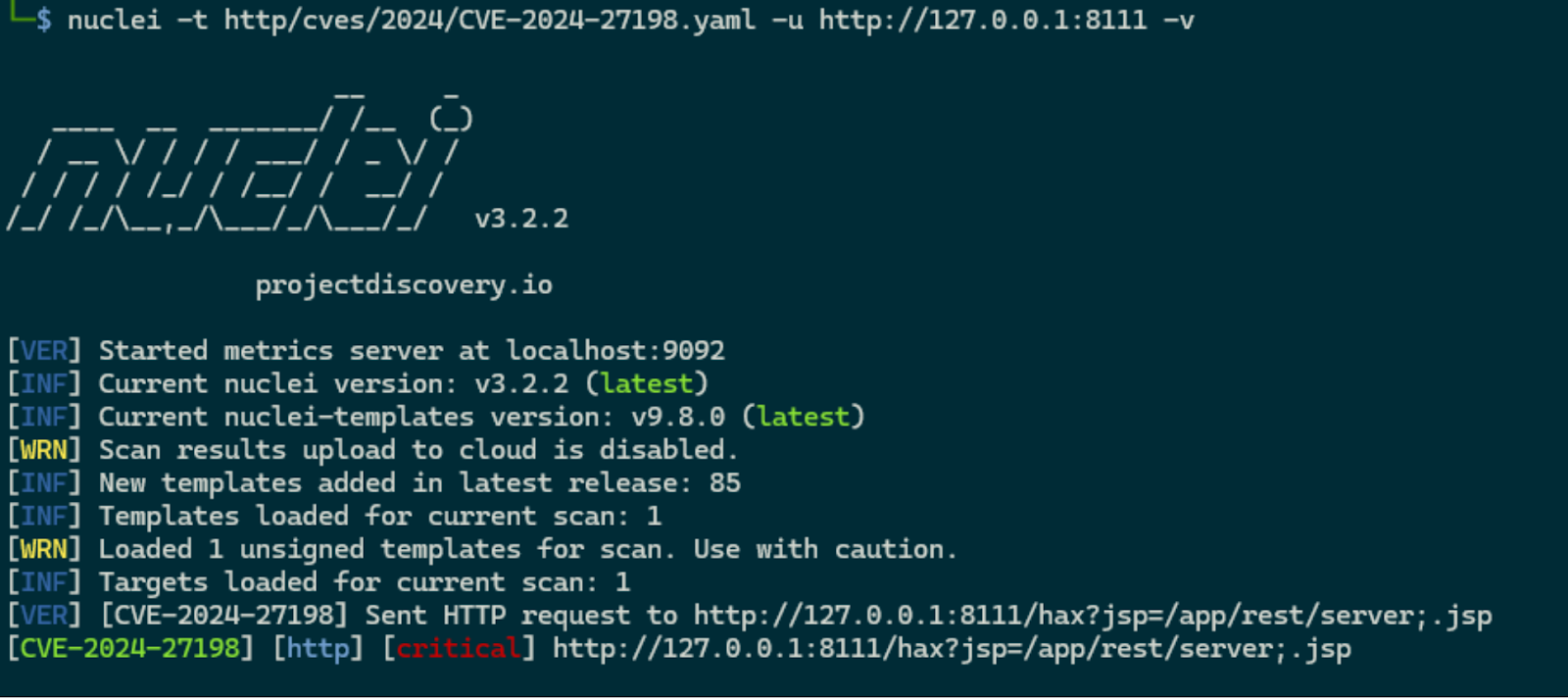
Following Rapid7’s official disclosure post, it is possible to check the exploitability of an asset by performing a curl request, such as:
curl -i ‘http://127.0.0.1:8111/hax?jsp=/app/rest/server;.jsp’.
Following the responsible and coordinated disclosure between JetBrains and the cybersecurity platform Rapid7, numerous detection scripts and exploit examples quickly emerged on GitHub.
A nuclei template was also released, which can quickly identify risks and threats to a vulnerable asset by performing a check like the one conducted manually.
Indicators of Compromise (IOCs)
Indicators of Compromise (IOCs) are specific details that help to identify potential unauthorized or malicious activity within your systems.
By default, the TeamCity log files are located in “C:\TeamCity\logs\” on Windows and “/opt/TeamCity/logs/” on Linux.
The following are examples of IOCs for the two vulnerabilities in question:
Access token creation
If the malicious actor has created and deleted an access token to exploit the vulnerability to gain access, they may leave traces in the “teamcity-javaLogging” log file. If the unauthorized user has been deleted afterward, both the “teamcity-server.log” and the “teamcity-activities.log” could contain audit activities that indicate that they have been deleted.
Malicious plugins
Uploading malicious plugins may record successive lines, in both the “teamcity-server.log” and the “teamcity-activities.log”, indicating the plugin was uploaded and subsequently deleted.
There may also be residual artifacts in the TeamCity Catalina folder, webapps plugin folder, or the TeamCity data directory.
Audit log
The TeamCity administration console contains an audit page that will display the deletion of an access token, the upload and deletion of a plugin, and the creation of an admin account. This audit log is stored in the internal database data file “buildserver.data”.
Recommendations
The Ackcent cybersecurity team strongly recommends upgrading to the latest version of TeamCity and continuing to follow our technical analyses of the latest critical threats that affect businesses and organizations around the world.
Contact our team of security experts to find out how Ackcent’s MDR services can help your organization manage cybersecurity incidents.